In today’s world, keeping company information safe is more important than ever. Many threats come from outside, but sometimes the danger is from inside the company. That’s where an insider threat program comes in. It helps businesses find and stop threats from within. But what is the goal of an insider threat program? This article will explain everything you need to know—in simple words that even a 10-year-old can understand.
What Is the Goal of an Insider Threat Program?
The main goal of an insider threat program is to protect a company from people inside the organization who might cause harm, either on purpose or by mistake. These people could be employees, contractors, or anyone who has access to the company’s systems or data.
Sometimes, insider threats happen when someone is unhappy with the company and wants revenge. Other times, they don’t mean to cause harm—they just make a mistake, like clicking on a dangerous email link or sharing private data by accident.
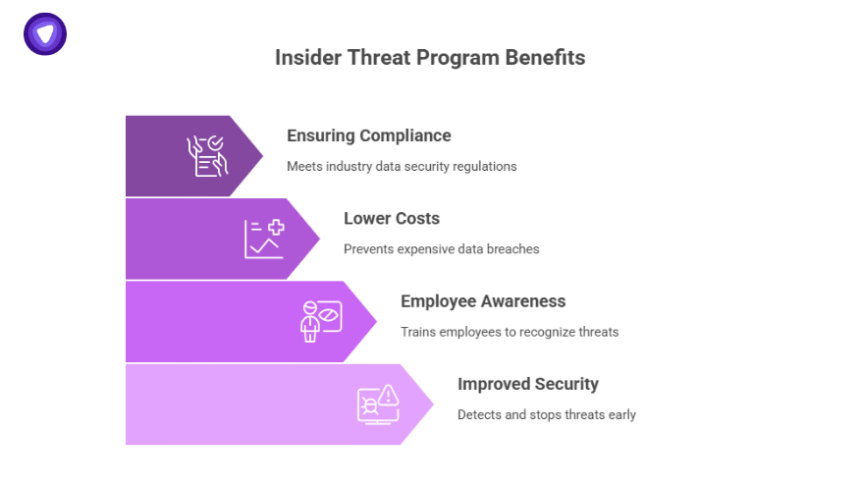
The insider threat program works to spot these problems early and stop them before any real damage is done. It also helps train employees, monitor behavior, and use smart tools to detect anything strange. Companies want to protect their data, money, and reputation—and that’s why this kind of program is so important.
Why Do Companies Need These Programs?
Companies need insider threat programs because most cybersecurity programs focus only on outside attacks, like hackers. But insider threats are just as dangerous—and sometimes even worse.
Imagine a bank employee who knows how to bypass security or a healthcare worker who can see patients’ personal information. These insiders already have access, so they don’t need to break in like a hacker would. That makes them harder to detect and stop.
Insider threats can lead to:
- Data breaches
- Financial loss
- Legal problems
- Loss of customer trust
- Damage to the company’s brand
An insider threat program helps reduce these risks by watching closely for warning signs, educating staff, and reacting quickly when a threat is found.
How Does an Insider Threat Program Work?
An insider threat program is like a smart security guard that watches what’s going on inside a company. It does this in several ways:
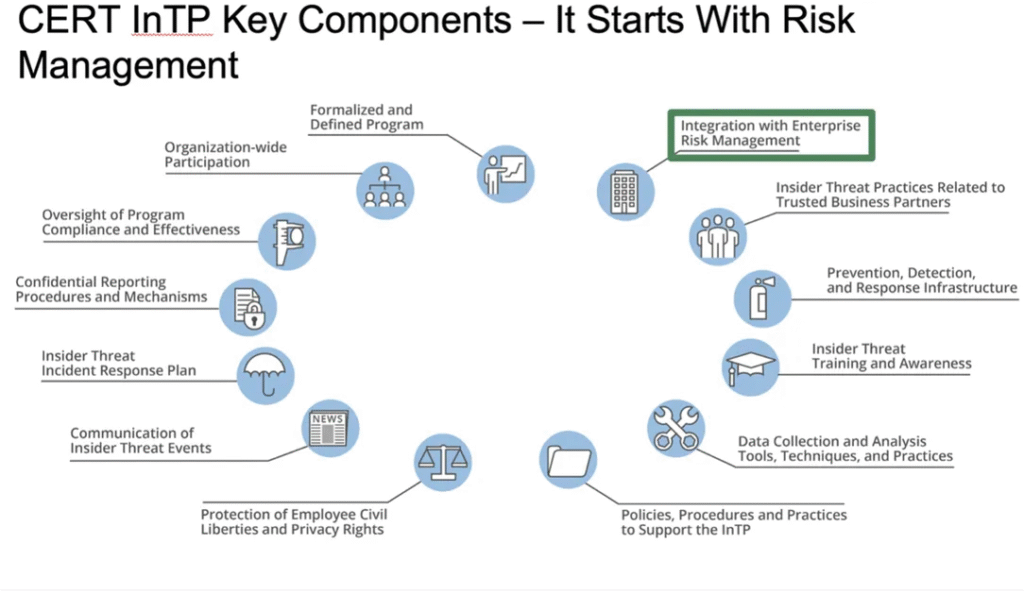
- It monitors employees’ behavior to see if anything unusual happens.
- It trains people to understand the risks and avoid making dangerous mistakes.
- It uses advanced technology to catch threats early.
All these parts work together to protect the company from internal risks.
Watching for Risky Behavior
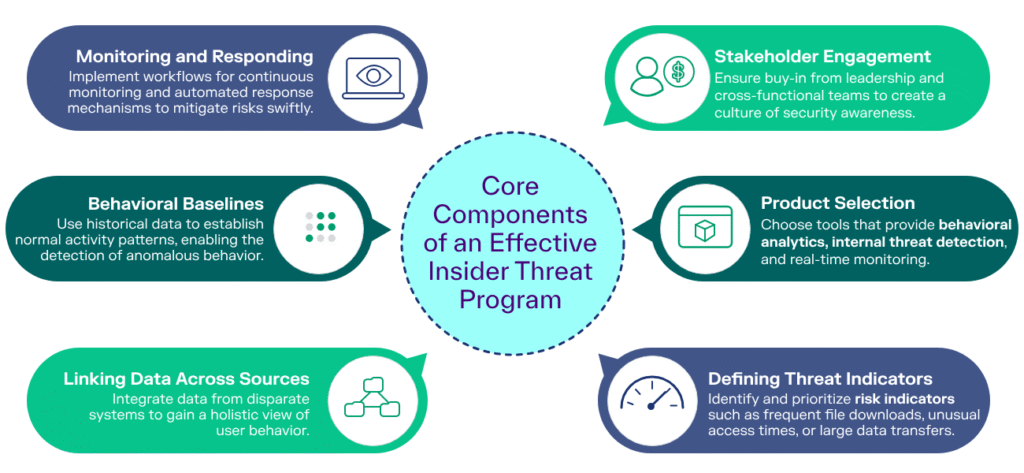
One important job of the program is to look for unusual behavior. For example, if someone starts accessing files they don’t normally use, or if they log in at strange hours, that could be a red flag.
The program sets up systems that send alerts when this kind of behavior happens. It doesn’t mean the person is guilty—it just means the company should take a closer look.
Training Employees to Be Careful
Training is a huge part of any insider threat program. Many insider threats happen by accident. Someone might forget to lock their computer, send sensitive data to the wrong person, or fall for a phishing email.
The program helps employees learn safe habits, like:
- Using strong passwords
- Not clicking on unknown links
- Reporting strange emails or behavior
The goal is to make every employee part of the security team.
Using Technology to Help
Technology plays a big role in stopping insider threats. Tools like:
- User behavior analytics (UBA)
- Data loss prevention (DLP)
- Access control systems
- SIEM (Security Information and Event Management)
These tools collect data, watch for odd activity, and alert security teams if something seems wrong. This kind of technology is like having eyes on everything, all the time.
Who Can Be an Insider Threat?
An insider threat isn’t always a “bad guy.” It can be anyone who has access to a company’s systems or sensitive information. This includes:
- Full-time employees
- Part-time workers
- Contractors or freelancers
- Former employees with leftover access
- Business partners
Even someone who means well can become a threat. For example, a tired employee might accidentally send a customer’s private data to the wrong person. Or a stressed-out worker might copy files they don’t need.
That’s why the insider threat program doesn’t just focus on catching “bad” people—it works to prevent mistakes and stop damage before it happens.
Types of Insider Threats You Should Know
There are different kinds of insider threats. Understanding them can help companies better prepare and respond.
- Malicious Insider – This is someone who intentionally tries to harm the company. They might steal data, share secrets with competitors, or delete important files.
- Negligent Insider – These people don’t mean to cause harm, but their actions are careless. For example, they might use weak passwords or forget to log out of systems.
- Compromised Insider – Sometimes, an outsider takes over an employee’s account without them knowing. This can happen through phishing or malware. The insider becomes a threat without realizing it.
- Departing Employee – When someone is leaving a company, they might take information with them. Even if they don’t plan to misuse it, having that data outside the company is a risk.
Each of these types needs a different kind of response, and a strong insider threat program can help handle them all.
Signs of a Possible Insider Threat
Insider threats don’t always show up in obvious ways, but there are some warning signs that companies can watch for. Here are a few common ones:
Sudden Behavior Changes
If an employee suddenly becomes very secretive, aggressive, or withdrawn, it might be a sign of something wrong. Of course, not every mood change is a threat—but it’s worth paying attention to.
For example, if someone is usually friendly and open, but then stops talking to coworkers and starts acting strange, it could be a red flag.
Accessing Strange Files
Another warning sign is when someone starts looking at files or systems they normally don’t need. For instance, a marketing employee who starts accessing financial data or HR files might raise concern.
These actions are tracked by security tools and flagged for further review.
Ignoring Security Rules
Employees who often break the rules can become risks. They might:
- Share passwords
- Disable security settings
- Use personal devices without permission
Even small rule-breaking can lead to big problems, especially if it becomes a pattern.
How to Stop Insider Threats Before They Happen
Stopping insider threats before they happen is the best way to protect a company. That means focusing on prevention, not just reaction. Here’s how companies can do that:
- Train everyone regularly so they understand risks and how to avoid them.
- Set clear rules about who can access what data.
- Use smart tools to monitor behavior and catch strange activity early.
- Create a culture of trust and safety, where employees feel comfortable reporting concerns.
- Limit access to only what each employee needs for their job.
Prevention is always easier—and cheaper—than cleaning up after a data breach.
The Bottom Line
So, what is the goal of an insider threat program? It’s simple: To protect a company from the risks that come from within. Whether someone is acting with bad intentions or just making a mistake, these programs help find and stop problems before they cause real damage.
An insider threat program watches for warning signs, trains employees, and uses smart technology to keep data safe. It helps businesses stay strong, avoid costly problems, and build trust with customers and partners.
In today’s digital world, every company needs an insider threat program. It’s not just for big tech firms or banks—it’s for schools, hospitals, stores, and more. If someone can access your systems, they can be a risk.